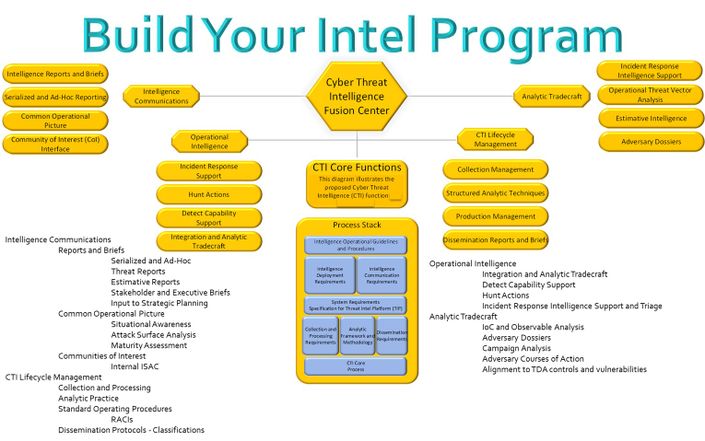
Building and Enhancing Your CTI Program with Strategic Intelligence Analysis - The Formula!
Build and Enhance Your CTI Program - Intensive and In-depth Hands-on - 10 Additional Lectures with Templates and Examples - Learn and Build at the same time
Watch Promo Enroll at the bottom of this page.Building and Enhancing Your CTI Program with Strategic Intelligence Analysis - The Formula!
Build a mature cyber intelligence program without guesswork. Follow a proven path from first charter to operational delivery across planning, collection, analysis, production, and review.
Start Now (scroll to the bottom to enroll) Preview SyllabusOutcome-Driven
”Taken from the headlines” real artifacts during the course: strategy, SOPs, maturity map, collection plan, reporting templates, and stakeholder comms.
Field-Tested
Adopt methods shaped across sectors and continents with repeatable steps and clear checkpoints.
Mentored
Receive expert feedback on deliverables with structured peer review and actionable guidance.
Your Finished Stack
Program Fit
| Need | Building and Enhancing Your CTI Program with Strategic Intelligence Analysis - The Formula! | Generic Training |
|---|---|---|
| Produce real artifacts | Included with reviews | Slides without outputs |
| Bias-aware analysis | ACH and SATs applied | High-level references |
| Executive alignment | Measurable outcomes | Unclear next steps |
Syllabus Preview (scroll towards the bottom for the complete syllabus)
Foundation → Charter, Mandate, and Outcomes
Adversary & Stakeholder Mapping
Collection Planning & SATs
Program Development & SOPs
Production, Delivery & Review
Outcomes From Learners
— Program Manager, Financial Services
— CTI Lead, Manufacturing
Instructor
Access videos, templates, examples, and reviews. Progress at your pace with scheduled office hours from instructors.
Your Instructor

Treadstone 71 is a woman and veteran-owned small business exclusively focused on cyber and threat intelligence consulting, services, and training. We are a pure-play intelligence shop.
Training dates and locations here
Since 2002, Treadstone 71 delivers intelligence training, strategic, operational, and tactical intelligence consulting, and research. We provide a seamless extension of your organization efficiently and effectively moving your organization to cyber intelligence program maturity. Our training, established in 2008, follows intelligence community standards as applied to the ever-changing threat environment delivering forecasts and estimates as intelligence intends. From baseline research to adversary targeted advisories and dossiers, Treadstone 71 products align with your intelligence requirements. We do not follow the create once and deliver many model. We contextually tie our products to your needs. Intelligence is our only business.
- We use intuition, structured techniques, and years of experience.
- We supply intelligence based on clearly defined requirements.
- We do not assign five people to do a job only one with experience.
- We do not bid base bones only to change order you to overspending.
We are known for our ability to:
- Anticipate key target or threat activities that are likely to prompt a leadership decision.
- Aid in coordinating, validating, and managing collection requirements, plans, and activities.
- Monitor and report changes in threat dispositions, activities, tactics, capabilities, objectives as related to designated cyber operations warning problem sets.
- Produce timely, fused, all-source cyber operations intelligence and indications and warnings intelligence products (e.g., threat assessments, briefings, intelligence studies, country studies).
- Provide intelligence analysis and support to designated exercises, planning activities, and time-sensitive operations.
- Develop or recommend analytic approaches or solutions to problems and situations for which information is incomplete or no precedent exists.
- Recognize and mitigate deception in reporting and analysis.
Assess intelligence, recommend targets to support operational objectives. - Assess target vulnerabilities and capabilities to determine a course of action.
- Assist in the development of priority information requirements.
- Enable synchronization of intelligence support plans across the supply chain.
- ...and Review and understand organizational leadership objectives and planning guidance non-inclusively.
